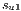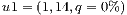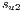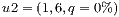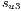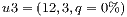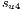Servicios Personalizados
Revista
Articulo
Links relacionados
Compartir
CLEI Electronic Journal
versión On-line ISSN 0717-5000
CLEIej vol.18 no.3 Montevideo dic. 2015
Quality of Protection on WDM networks
A Recovery Probability based approach
Abstract
WDM networks survivability needs a flexible quality of protection (QoP) due to the variety of existing connection demands, lack of fair resource distributions under traditional QoP and optimal resources assignment. Thus, this paper proposes a new paradigm of QoP based on generic levels of protection where the set of protection levels can be defined as the network administrator needs, i.e., a flexible QoP approach whose particular case is the traditional or non-flexible QoP approach. Essentially, the proposed generic level is based on the recovery probability concept which measures the grade of conflict among primary lightpaths that share backup lighpaths for link failure recovery. In order to study how this strategy impacts on the network cost, a Genetic Algorithm is proposed. It calculates the primary and backup lightpaths, considering a multi-objective optimization on the basis of lexicographical sorting approach. The Genetic Algorithm minimizes the number of blocked requests, the number of services without protection, the total differences between the requested QoP and the assigned QoP, and the network cost; all of which by considering the optical fibers used and subject to the wavelength usage as constraint. The experimental results indicate that the proposed approach –flexible QoP– is a promising strategy where the network cost, the number of requests and QoP levels are contradictory objective functions in environments with homogeneous and heterogeneous QoP requirements.
Abstract in Spanish
La supervivencia de redes WDM necesita una calidad de protección (QoP) flexible debido a la variedad de demandas existentes, la falta de distribución equitativa de recursos bajo la tradicional QoP y la asignación óptima de recursos. Así, este paper propone un nuevo paradigma de QoP basado sobre niveles genericos de protección donde el conjunto de niveles de protección pueden ser definidos acorde a las necesidades del administrador de la red, esto es, un enfoque QoP flexible cuyo caso particular es el enfoque tradicional o QoP no flexible. Esencialmente, el nivel generico propuesto se basa sobre el concepto de probabilidad de recuperación el cual mide el grado de conflicto entre caminos primarios que comparter caminos de resguardos para la recuperación de falla de enlace. Para estudiar como esta estrategía impacta sobre el costo de la red, un Algoritmo Genético es propuesto. Éste calcula los caminos primarios y de resguardo, considerando optimización multi-objetivo sobre la base del enfoque de ordenamiento lexicográfico. El Algoritmo Genético minimiza el número de solicitudes bloqueadas, el número de servicios sin protección, la diferencia total entre la QoP asignada y la QoP solicitada, y el costo de la red; todo esto considerando el uso de la fibra óptica y sujeto a la restricciones de uso de longitud de onda. El resultado experimental indica que el enfoque propuesto -QoP flexible- es una estrategía promisoria donde el costo de la red, el número de solicitudes y los niveles QoP son funciones objetivos contradictorias en ambientes con requerimiento QoP homogéneo y heterogéneo.
Keywords: WDM networks, Recovery Probability, Quality of Protection, Genetic Algorithms.
Keywords in Spanish: Redes WDM, Probabilidad de Recuperación, Calidad de la Protección, Algoritmos Genéticos.
Received: 2014-12-01 Revised: 2015-10-29 Accepted: 2015-11-07.
1 Introduction
Optical networks based on WDM (Wavelength-Division Multiplexing) technology are the main way for high performing communication [1, 2, 3, 4, 5, 6, 7, 8, 9]. WDM networks have associated three fundamental aspects: design, administration, and survivability [1, 10]. Within these aspects a key point is the service types which can be determined by: the quantity of sources and destinations, the quality of service (QoS), the failure types, the recovery schemes, among others [1, 3, 11, 12, 13]. Basic QoS classifications have been reported by several studies [2, 4, 8, 9, 14] without considering fairness distribution and optimal resources allocation. However, there is a need to use the QoS requirement to ensure the communication recovery. This is called the quality of protection (QoP) [4]. Another critical aspect is the services diversity growing with QoP requirement, which cannot find quick answer with the traditional scheme of QoP classification [2, 4, 8, 9, 14]. As a result, a new paradigm QoP must be developed in order to meet the diversity of QoP requirements in a simple and easy way. On this basis, the main contribution of this work proposes a flexible QoP strategy based on recovery probability for simple link failure scenarios. Firstly, this approach is compared with traditional QoP strategies (non-flexible schemes) in the routing and wavelength assignments with protection against simple link failures (RWA-PLF) problem as a case of study. Through this simple experiment we show the benefit of the QoP flexible scheme proposed from the user perspectives. Secondly, in order to study the behavior of routing cost when parameters of requests and QoP levels change, a Genetic Algorithm inspired in [2] is proposed to solve the RWA-PLF problem, considering the flexible QoP strategy and several scenarios. Basically, we want to optimize the cost of primary and backup lightpaths of a set of unicast requests, subject to its QoP requirements and a pre-defined set of QoP levels.
This document is organized as follows: Section 2 briefly presents failure management schemes. Section 3 introduces concepts of QoS and QoP. The proposal of flexible QoP is given in Section 4 while the proposed Genetic Algorithm is exposed in Section 5. Section 6 presents and discusses experimental results, and finally, in Section 7 our conclusions and future work are given.
2 Failures Management Schemes
Literature reports various failure types: node and link failures, and shared-risk resource group [15]. This work focuses on link failures, considering a single point of failure or a simple failure. Generally, WDM networks are vulnerable to link failure with catastrophic consequences since large volume of traffic is lost in a very short time. These link failures happen due to fiber cuts and hardware device failures such as: receivers, laser, amplifiers, routers and converters. The reports indicate that one kilometer of cable is damaged after 228 years (4.39 cuts/year/1000 kilometers) [12]. Therefore, WDM networks survivability is a critical issue. Consequently, networks survival strategies have been developed defining alternative paths in case of failures. Under these circumstances, various static and dynamic protection paradigms have been proposed [1, 16]. The following classification is primary for this work:
- Survival techniques indicate the moment in which the backup path is calculated.
- Protection-oriented survival [1, 2]: primary and backup paths are calculated in the design time. Two approaches can be identified according the shared resource type:
- Dedicated protection (1+1): the backup path’s assigned resources cannot be used on other demands.
- Shared protection (M:N): M backup paths protect N primary paths; i.e. the resources of backup paths can be used by other primary services.
- Restoration-oriented survival: The backup path is calculated after the primary path failures without warranty; i.e. the best effort.
- Protection-oriented survival [1, 2]: primary and backup paths are calculated in the design time. Two approaches can be identified according the shared resource type:
- Survivability path section defines the sections of the primary path to be protected in a way independently.
- Path-oriented protection: a backup path protects the complete primary path.
- Link-oriented protection: a backup path protects a link of the primary path. There will be as many backup paths as links in the primary path.
- Segment-oriented protection: a backup path protects a segment of primary path; therefore, there will be as many backup paths as pre-defined segments in primary path.
Let us note that link and path-oriented protections are particular cases of segment-oriented protection. Protection schemes change their structures depending on whether the traffic is unicast or multicast. A good classification can be seen in [17]. Another aspect to consider is how to evaluate the performance of networks survivability. In [18], resources efficient usage, failure recovery time, and complexity of structure are network survivability measures.
3 Quality of Protection
For an Internet service provider, the cost depends on the physical layout and the network operation. There are different rates according to QoS level. These rates are sensible to data volume, time (day/night), priority, delay, data loss, and other factors called QoS parameters [1].
Huang et al. [7] present the routing and protection problem with QoS requirements as constraints. They divide the network QoS metrics into two categories: additive and bottleneck. For example, the path delay is given by summing up the delays of all the links on the path and it is called additive metric. Another example is the path loss rate, which is the product of the loss rate of all the links on this path. However, we can use the logarithm of loss rate to denote the loss rate. In that case, we can also consider the loss rate as an additive metric. On the other hand, the bandwidth is a bottleneck metric, since the bandwidth of a path is the minimum of the bandwidth of all links on the path.
Various works [2, 4, 8, 9, 14] have reported basic QoP classifications. Gerstel et al. [8] suggest Quality of Protection (QoP) paradigm where protected-dedicated and unprotected-dedicated primary paths are considered. The concept of QoP is proposed for the first time in [8] as an extension of QoS, but they do not define how to quantify the QoP.
Zhong et al. [14] present a basic QoP proposal based on lineal programming to establish paths in a WDM network dynamically. It defines QoP levels based on the exclusivity of assigned paths:
- Level 2: Link-disjoint primary and backup paths. Both are dedicated and pre-calculated (protection-oriented survival).
- Level 1: Link-disjoint primary and backup paths. Just the primary path is dedicated and pre-calculated; if a primary path failures, a backup path is calculated (restoration-oriented survival).
- Level 0: Only non-dedicated primary paths without protection are provided; i.e. primary path can be preempted by other paths.
At this point, it is important to highlight the conclusion stated in [14]: the allowance of multiple levels of service leads to higher performance in terms of resource use and reduces the number of blocked connections.
Similarly, Kim et al. [19] indicate that 5-levels QoP solutions let up to 30% in cost saving in comparison to solutions without QoP levels; and up to 8% by using just 2 levels instead of 5. Two key aspects are observed in that work: (a) the importance of multiple QoP levels; and (b) the optimal determination number of QoP levels.
Kim et al. [19] propose protection levels as follows:
- Priority Class (Class A): Dedicated-path protection (1:1 or 1+1).
- Protected Class (Class B): Shared-path protection (1:N).
- Reroutable Class (Class C): The shortest path is assigned as primary without protection; however, when a failure happens, then a backup path is calculated if it were possible.
- Unprotected Class (Class D): The shortest path is assigned as primary without protection and rerouted.
- Preemptable Class (Class E): Resources of primary path can be preempted by other paths.
Nuñez et al. [2] proposed a 3-levels QoP scheme (gold, silver, and bronze), according to the exclusivity of protection resources:
- Gold level (1+1): Link-disjoints primary and backup paths, both are dedicated and pre-calculated.
- Silver level (1:1): Link-disjoints primary and backup paths. Primary path is dedicated and pre-calculated, and backup path is shared and pre-calculated. In case of primary path failures, the backup is used.
- Bronze level: Only a pre-calculated and non-dedicated primary path is provided.
Pujo et al. [9] propose a QoP based on the delay differentiation, in which many parameters are reported to be considered. Assigning superior priority to certain traffic degrades the capabilities of the inferior priority traffic.
On the basic of works [8, 14, 19, 2, 9] the concept of QoP in this work is extended to fixed levels to flexible QoP for WDM networks protection, considering dedicated-shared protection schemes. In this context, each exposed work is a particular case of the flexible QoP level strategy that will be presented in the next section.
4 Proposal
This work is developed in the field of WDM networks where the optical channels can contain multiple optical fibers and wavelengths. Furthermore, we suppose that each network node has full capacity of wavelength conversion. This proposal focuses on the RWA-PLF problem, where routing algorithms, wavelength assignment strategies and protection schemes are keys. In this context, the following features are considered: (1) unicast requests; (2) static traffic; (3) wavelength usage constraint; (4) full capacity of wavelength conversion on all nodes; (5) simple-link failures; (6) segment-oriented protection scheme; and (7) protection-oriented survival. Firstly, to understand the flexible QoP concept, we need to define the symbols used.
4.1 Symbolic Representation
For this work, a WDM network is modeled as a graph 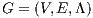 , where
, where 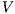 is the set of nodes,
is the set of nodes, 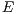 is the set of links, and
is the set of links, and 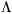 is the set of available wavelengths on each optical link belonging to
is the set of available wavelengths on each optical link belonging to 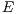 . Be:
. Be:

4.2 QoP flexible in WDM networks
The proposed strategy is to determine generic QoP levels by means of the recovery measure 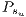 of the primary lightpaths. This strategy only considers protection-oriented survival. Generically, the set of levels is as follows:
of the primary lightpaths. This strategy only considers protection-oriented survival. Generically, the set of levels is as follows:
- Priority service: exclusive primary and backup lightpaths (1+1). Maximum recovery measure
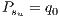 = 100 % (dedicated protection).
= 100 % (dedicated protection). - Protected service with
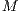 levels: exclusive primary lightpath and shared backup lightpath with recovery measure
levels: exclusive primary lightpath and shared backup lightpath with recovery measure 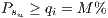 where
where 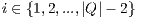 . Each link of the backup lightpath can be shared with other backup lightpaths. In this context, the shared setting 1:
. Each link of the backup lightpath can be shared with other backup lightpaths. In this context, the shared setting 1: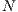 is a special case where
is a special case where 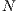 backups use the same lightpaths (shared protection).
backups use the same lightpaths (shared protection). - Preemptible service: primary lightpaths which components can be used by other backup lightpaths, it is clear that recovery measure for this service is
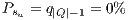 .
.
The Table 1 shows the comparison among the state-of-the-art approaches and our proposal. This comparison is a bit complex because protection levels and restoration are handled at the same time. The highest priority service has dedicated protection as shown in row 1 (Table 1).
Different shared protection levels are listed in rows 2, 3, and 5. Row 4 (for Proposals 1 and 3) shows services without protection but with restoration. While in row 6 the lowest priority level is presented. The maximum QoP level (based on the scheme 1+1) can be observed in the intersection of the flexible QoP column and row 1. Finally, in the rows 2 to 6 are presented QoP levels ranging from 0% (unprotected and preempted) to 100% (1:1) of warranty recovery. This work focuses on the network survival design phase. Therefore, only protection schemes are considered. Note that, there might be as many QoP levels as needed in comparison to fixed classes in proposals 1, 2, and 3 [2, 14, 19]. Note that, each QoP class defined in [2, 14, 19] are particular cases of this paper’s proposal.
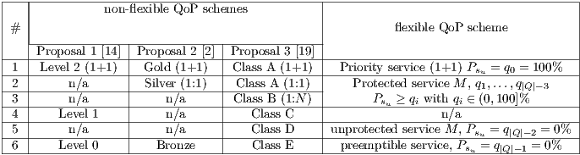
Another worthy important aspect to mention is that the works [2, 14] and [19] only consider path-oriented protection schemes, while in this work a segment-oriented protection scheme is applied, being more efficient than any other one.
Finally, with this flexible scheme of QoP levels, the following essential points are achieved:
- Flexibility is given to the owners of the networks to create as many levels of services as they consider appropriate and not just fixed schemes like proposals 1, 2, and 3 (Table 1).
- Resource usage improvement [19].
4.3 Link Recovery Probability
Before evaluating the recoverability of a service 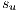 , the recovery probability
, the recovery probability 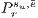 of a link
of a link 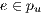 must be evaluated. This probability is calculated with respect to the number of services that share protection resources; therefore, the following definition is given:
must be evaluated. This probability is calculated with respect to the number of services that share protection resources; therefore, the following definition is given:
Definition 1 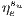 is the number of services
is the number of services 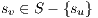 that share protection resources when a link
that share protection resources when a link 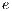 is used simultaneously by primary lightpaths
is used simultaneously by primary lightpaths 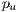 and
and 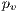 with
with 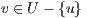 .
.
The range of values of 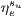 is between
is between 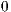 and
and 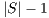 where
where
 | (1) |
Then, 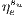 can be calculated as follows:
can be calculated as follows:
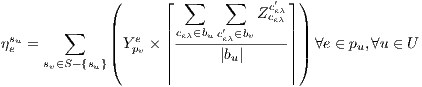 | (2) |
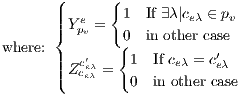 |
In this context, the link recovery probability 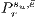 of a primary path
of a primary path 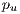 , in case the link
, in case the link 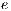 fails can be calculated as:
fails can be calculated as:
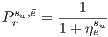 | (3) |
Note that, if a service 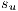 does not conflict with other services when the link
does not conflict with other services when the link 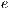 fails then
fails then 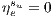 and the recovery probability is
and the recovery probability is 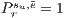 (100%). Conversely, at higher conflicts for the resources, the probability tends to 0, given that
(100%). Conversely, at higher conflicts for the resources, the probability tends to 0, given that 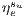 increases to
increases to 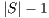 . Furthermore, in (3) we suppose that all competitors are equally likely to take protection resource; i.e., there is no priority.
. Furthermore, in (3) we suppose that all competitors are equally likely to take protection resource; i.e., there is no priority.
4.4 Service recovery measurement
The recovery measure of a service can be computed with the expressions (2) and (3). Now we proceed to calculate the recovery measure 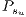 .
.
Formally, 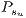 is set to:
is set to:
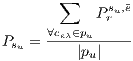 | (4) |
where 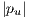 is the number of optical links in the path
is the number of optical links in the path 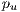 .
.
The expression (4) is the measure used in this work to define the QoP levels of a service when a link fails. At this stage, it is important to consider that the criterion (4) is a valid measure as well as it can be the maximum and minimum link recovery probability and other criteria.
4.5 Mathematical Formulation
Using the above definitions, the RWA-PLF with QoP requirement problem can be treated in a multi-objective optimization context based on lexicography approach. Given a network topology 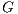 , a set of requests
, a set of requests 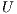 , a vector of links cost
, a vector of links cost 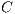 , and a set of available services
, and a set of available services 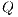 , this problem aims to calculate the solution
, this problem aims to calculate the solution 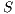 that minimizes the number of blocked requests
that minimizes the number of blocked requests 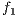 , the amount of services without protection
, the amount of services without protection 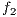 , the difference in levels between the requested and obtained QoP
, the difference in levels between the requested and obtained QoP 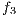 , and the routing cost
, and the routing cost 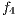 . The last objective function (
. The last objective function (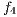 ) is the network cost considering used optical fibres in primary and backup lightpaths. The problem is stated as follows:
) is the network cost considering used optical fibres in primary and backup lightpaths. The problem is stated as follows:
![⊤ minf = [f1,f2,f3,f4]](/img/revistas/cleiej/v18n3/3a0258x.png) | (5) |
such that:
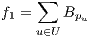 | (6) |
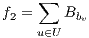 | (7) |
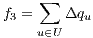 | (8) |
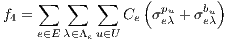 | (9) |
 |
subject to the wavelength usage constraint:
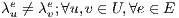 | (10) |
Note that, the constraint (10) implies that 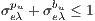 and defines whether a link
and defines whether a link 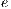 is used by a primary or backup of a request
is used by a primary or backup of a request 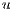 . Furthermore, the constraint (10) indicates that each
. Furthermore, the constraint (10) indicates that each 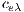 is used in just one ligthpath. This is important because conflicts arise among services with shared lightpaths that can not simultaneously use an optical channel.
is used in just one ligthpath. This is important because conflicts arise among services with shared lightpaths that can not simultaneously use an optical channel.
5 Optimizer Algorithm
An elitist Genetic Algorithm [20] named Flexible Levels Service Algorithm (FLSA) is proposed as a design tool. The FLSA is coded in Algorithm 1, while the evaluation of a solution is outlined in the Algorithm 2.
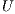 , set of available services
, set of available services 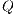 , network topology
, network topology 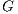 , genetic parameters and vector of links cost
, genetic parameters and vector of links cost 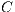 .
. OUTPUT: solution
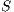 .
. 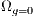 ; //generation
; //generation 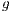
2: while Stop condition do not meet do
3: Evaluate each solution
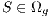 ; // Algorithm 2
; // Algorithm 2 4: Apply binary tournament to
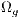 , obtaining
, obtaining 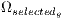 ;
; 5: Cross
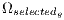 , obtaining
, obtaining 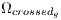 ;
; 6: Mutate
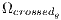 , obtaining
, obtaining 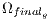 ;
; 7: Update best solution
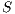 with
with 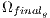 ;// Algorithm 3
;// Algorithm 3 8: Substitute
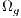 for
for 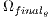 ;
; 9:
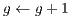
10: end while
11: Return
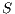
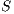 , set of request
, set of request 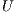 , set of available QoP levels
, set of available QoP levels 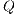 , vector of links cost
, vector of links cost 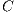
OUTPUT: objective functions
![S.f = [S.f1,S.f2,S.f3,S.f4]](/img/revistas/cleiej/v18n3/3a0293x.png) .
. 2:
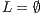 ; //initialize set of paths
; //initialize set of paths 3:
![S.f = [0,0,0,0]](/img/revistas/cleiej/v18n3/3a0295x.png)
4: for all
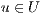 do
do 5: if primary path
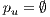 then
then 6:
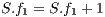 ; //calculation of (6)
; //calculation of (6) 7: else
8:
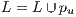 ;
; 9: if secondary path
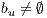 y
y 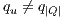 then
then 10:
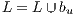 ;
; 11: else
12:
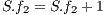 ; //calculation of (7)
; //calculation of (7) 13: end if
14: Calculate
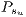 ; // with (4)
; // with (4) 15:
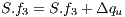 ; //calculation of (8)
; //calculation of (8) 16: end if
17: end for
18:
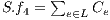 ; //calculation of (9)
; //calculation of (9) 19: Return
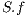 ;
; It is important to note that the four objective functions are evaluated in Algorithm 2. The best solution is update in line 7 of Algorithm 1, which was calculated in generation 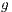 . This updating is made considering the lexicographical approach [21] according the procedure given by Algorithm 3.
. This updating is made considering the lexicographical approach [21] according the procedure given by Algorithm 3.
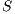 , population
, population 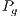
OUTPUT: the new best solution
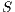
Note that, the objective functions 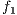 ,
, 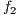 , and
, and 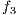 are usually considered as constraints [22], but in this implementation they are considered as objective functions together with the routing cost
are usually considered as constraints [22], but in this implementation they are considered as objective functions together with the routing cost 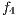 to give flexibility to the search of FLSA algorithm.
to give flexibility to the search of FLSA algorithm.
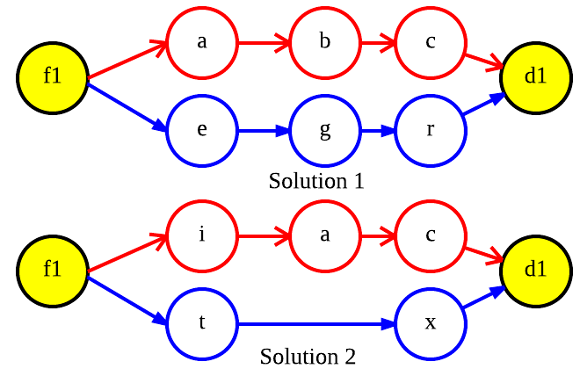
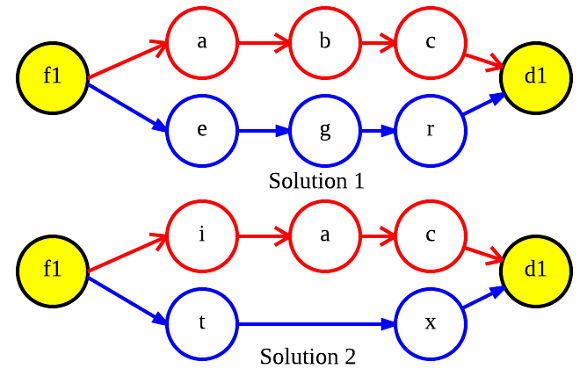
Chromosome. The proposed chromosome can be seen in Figure 1. 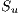 represents the chromosome and
represents the chromosome and 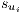 is the
is the 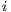 -th gene. Each gene encodes the solution for each unicast request
-th gene. Each gene encodes the solution for each unicast request 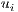 . Figure 2a presents an sample solution in the NSF network with a single request
. Figure 2a presents an sample solution in the NSF network with a single request 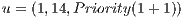 .
.
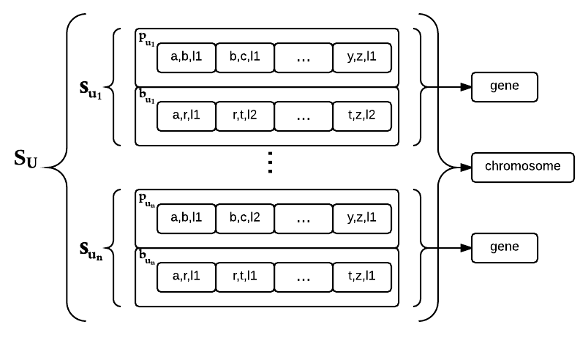
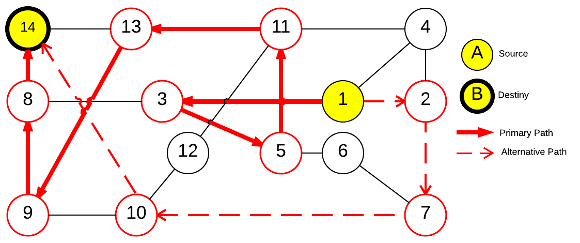
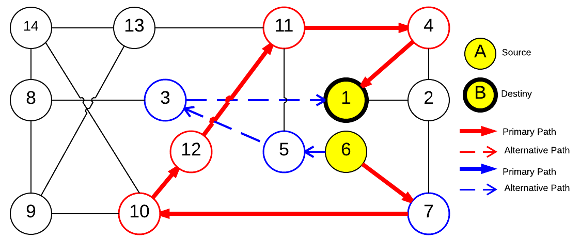
Primary and backup paths on NSF network.
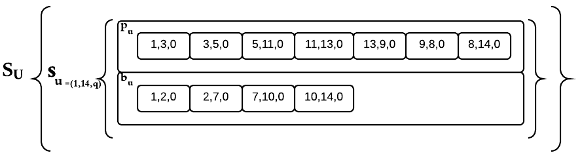
Primary and backup paths coded by chromosome.
Initial Population. Initial population 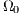 is randomly generated to obtain diversity at the beginning of the process. Each
is randomly generated to obtain diversity at the beginning of the process. Each 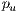 and
and 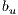 is made by selecting links and wavelengths randomly. Another important process is that the initial population is looking to get local information by two extreme solutions: (a) one solution is made up of the first and second shortest paths (path-oriented protection); and (b) in the other solution, the primary path is the shortest path while the backup path is made up of the shortest paths that protect each link of primary path (link-oriented protection).
is made by selecting links and wavelengths randomly. Another important process is that the initial population is looking to get local information by two extreme solutions: (a) one solution is made up of the first and second shortest paths (path-oriented protection); and (b) in the other solution, the primary path is the shortest path while the backup path is made up of the shortest paths that protect each link of primary path (link-oriented protection).
Selection. The selection operator in this work is the binary tournament [21]. Given two individuals that were selected at random, the best solution of them is taken as father. The comparison is performed lexicographically over the objective functions in the Algorithm 2.
Crossover. The crossover operator is performed on two parent chromosomes which were returned by the selection operator. An example of crossover can be seen in Figures 3a and 3b. Figure 3b shows the steps of crossing, in Step 1 the common nodes of both parents are selected. Step 2 applies the shortest paths computation for each pair of nodes. Step 3 calculates the shortest path from source to destination nodes as backup path. A null gene indicates path not found.
Mutation. This operator works with an occurrence probability of 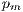 , where an individual is replaced by another new individual that is randomly generated.
, where an individual is replaced by another new individual that is randomly generated.
6 Experimental Results
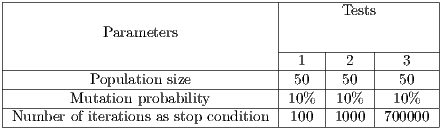
The proposed algorithm FLSA was implemented on a PC Intel i7-3630QM 2.40 GHz (x 8 threads) with 8GB of RAM, Javac Compiler 1.7.0. Several sets of unicast demands 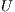 were selected for the NSF network. Each optical fiber has the same number of wavelengths. Basically, three types of experiments are conducted using the FLSA algorithm with the evolutionary parameters given in Table 2.
were selected for the NSF network. Each optical fiber has the same number of wavelengths. Basically, three types of experiments are conducted using the FLSA algorithm with the evolutionary parameters given in Table 2.
6.1 Test 1: Benefits of flexible QoP
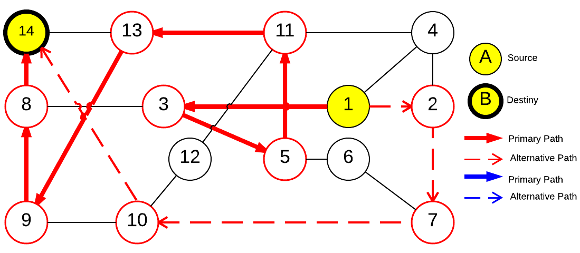
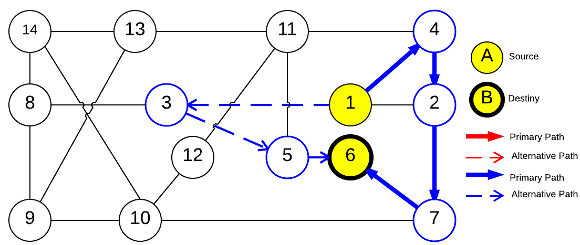
The objective of this test is to show the unfairness that happens when the protection is based on shared resources. In this context, the recovery measure 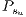 is calculated in such a way to be able to measure this value for all solutions, considering the requests of the Table 3.
is calculated in such a way to be able to measure this value for all solutions, considering the requests of the Table 3.
Algorithm FLSA was run once and the best solution was recorded. The primary and backup lightpaths of this solution are presented in Figures 4a, 4b, 4c, and 4d while their recovery measure 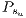 are listed in Table 3.
are listed in Table 3.
The results show how different services with the same QoP requirement (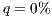 ) obtain different recovery measure values (Table 3). From practical viewpoint, all customers pay the same cost but they receive different service qualities.
) obtain different recovery measure values (Table 3). From practical viewpoint, all customers pay the same cost but they receive different service qualities.
 obtained in Test 1.
obtained in Test 1.
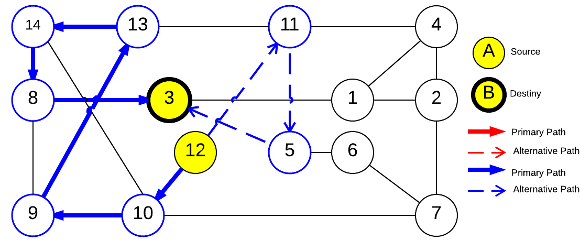
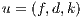 | 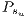 |
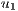 =(1,14,0%) =(1,14,0%) | 100.0% |
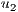 =(1,6,0%) =(1,6,0%) | 75.0% |
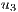 =(12,3,0%) =(12,3,0%) | 91.6% |
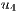 =(6,1,0%) =(6,1,0%) | 75.0% |
Conflicts over protection resources can be seen with the requests 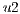 ,
, 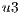 , and
, and 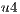 corresponding to the services
corresponding to the services 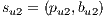 ,
, 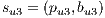 , and
, and 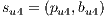 , since they have a
, since they have a 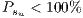 .
.
To understand the calculation of 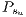 we can see the service
we can see the service 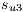 in Figure 6c. Then
in Figure 6c. Then 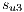 competes with the service
competes with the service 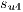 sketched in Figure 6d. Firstly, the primary lightpaths
sketched in Figure 6d. Firstly, the primary lightpaths 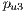 and
and 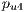 use optical link
use optical link 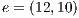 ; and secondly, the backup optical channel
; and secondly, the backup optical channel 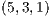 is assigned to lightpaths
is assigned to lightpaths 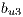 and
and 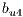 simultaneously. In this context, the calculation of the recovery measure of the service
simultaneously. In this context, the calculation of the recovery measure of the service 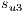 is as follows:
is as follows:
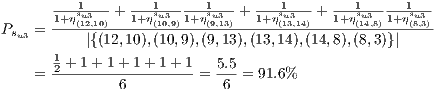
Applying the same procedure, 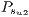 and
and 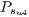 can also be calculated.
can also be calculated.
6.2 Test 2: RWA-PLF with homogeneous QoP requirements
Basically, the cost function will be studied considering 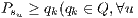 ). Four sets of unicast requests
). Four sets of unicast requests 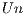 are generated, with (
are generated, with (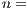 ) 10, 20, 30 and 40 requests, respectively. All requests have the same QoP level. At the same time, a set
) 10, 20, 30 and 40 requests, respectively. All requests have the same QoP level. At the same time, a set 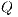 of six-levels requirement is considered where their schemes are defined by:
of six-levels requirement is considered where their schemes are defined by:
- priority service (1+1) corresponding to
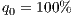 ;
; - protected services have the following values:
- level M1
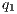 = 100% (1:1),
= 100% (1:1), - level M2
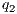 = 75%,
= 75%, - level M3
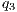 = 50%,
= 50%, - level M4
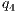 = 25%;
= 25%;
- level M1
- preemptible service
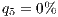 .
.
In this way, each one of these six levels will be used to evaluate the sets of traffic request 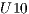 ,
, 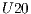 ,
, 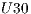 , and
, and 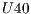 .
.
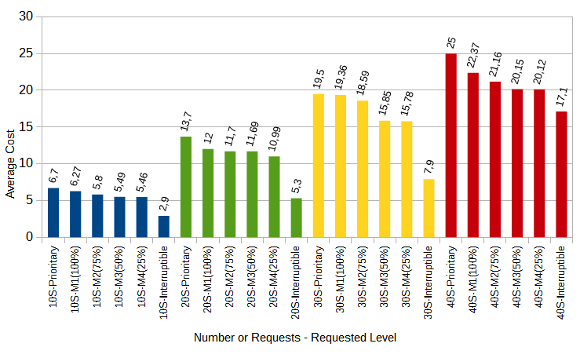
The algorithm FLSA is performed ten times for each test instance in the evaluation process to get the average costs as a preliminary study. The outcome for these tests shows when the number of request increases, then a higher recovery probability would be necessary and therefore a greater amount of resources.
Figure 5 presents results that indicate the number of requests and requested level separated by a dash. It can be seen that as QoP levels decrease, average costs also decrease. That is, the cost and QoP are objective functions in conflict. In addition, the correlation between the levels and costs for each set 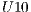 ,
, 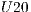 ,
, 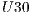 , and
, and 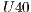 are
are 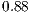 ,
, 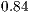 ,
, 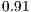 , and
, and 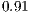 respectively. These correlations indicate the existence of a strong relationship between the requested QoP, and the average cost.
respectively. These correlations indicate the existence of a strong relationship between the requested QoP, and the average cost.
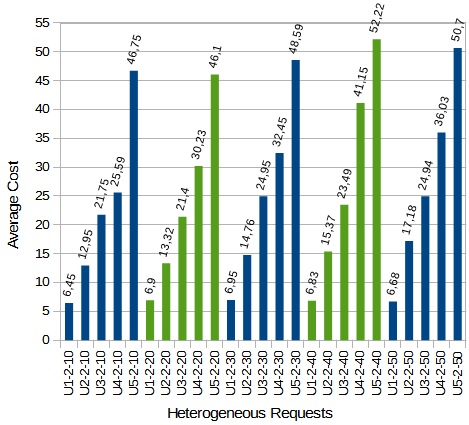
6.3 Test 3: RWA-PLF with heterogeneous QoP requirements
The set of requests was generated randomly under certain criteria according to:
- Number of Sessions (
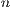 ): is the request connections number for each network node.
): is the request connections number for each network node. - Minimum Hops (
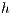 ): is the minimum distance between source and destination nodes; where the distance between adjacent nodes is fixed to one.
): is the minimum distance between source and destination nodes; where the distance between adjacent nodes is fixed to one. - Standard Deviation (
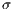 ): is the range of possible QoP values to apply, considering
): is the range of possible QoP values to apply, considering 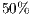 as medium value of the recovery probability, i.e.
as medium value of the recovery probability, i.e. ![q ∈ [0.5 - σ,0.5+ σ]](/img/revistas/cleiej/v18n3/3a02217x.png) .
.
For each source node a destination node is randomly selected according the previous criteria. For this experiment, the following values define the test cases:
- Number of Sessions (
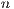 ): 1, 2, 3, 4, 5.
): 1, 2, 3, 4, 5. - Minimum Hops (
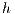 ): 1, 2, 3.
): 1, 2, 3. - Standard Deviation (
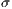 ): 10, 20, 30, 40, 50.
): 10, 20, 30, 40, 50.
In this way, 75 test cases with QoP levels requirements have been set, where the evaluation process is the same of the Test 2. On the other hand, a set 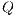 with twelve QoP levels is defined as follows:
with twelve QoP levels is defined as follows:
- priority service (1+1) corresponding to
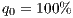 ;
; - protected service is conformed by:
- level M1
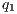 = 100% (1:1),
= 100% (1:1), - level M2
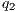 = 90%,
= 90%, - level M3
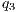 = 80%,
= 80%, - level M4
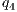 = 70%,
= 70%, - level M5
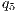 = 60%,
= 60%, - level M6
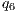 = 50%,
= 50%, - level M7
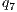 = 40%,
= 40%, - level M8
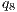 = 30%,
= 30%, - level M9
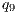 = 20%,
= 20%, - level M10
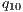 = 10%;
= 10%;
- level M1
- preemptible service
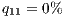 .
.
The results show that by increasing the parameters 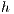 and
and 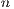 , the cost tends to increase, whereas if
, the cost tends to increase, whereas if 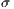 increases, the changes are not significant. The results are shown in Figures 6a, 6b, and 6c. For example: U1-2-10 represents all tests where applications meet with the Number of Sessions (
increases, the changes are not significant. The results are shown in Figures 6a, 6b, and 6c. For example: U1-2-10 represents all tests where applications meet with the Number of Sessions (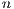 )=1, Minimum Hop (
)=1, Minimum Hop (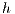 ) = 2, and Standard Deviation (
) = 2, and Standard Deviation (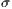 )=10 .
)=10 .
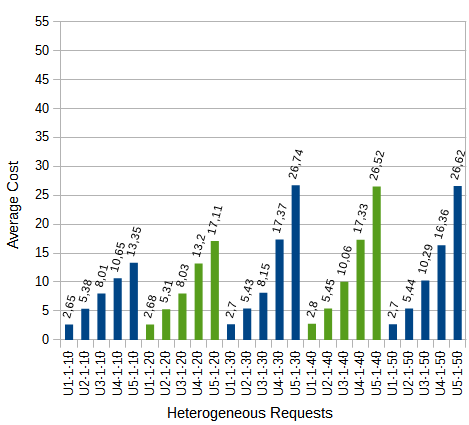
Average costs for requests Un-1- with heterogeneous QoP.
with heterogeneous QoP.
Average costs for requests Un-2-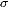 with heterogeneous QoP.
with heterogeneous QoP.
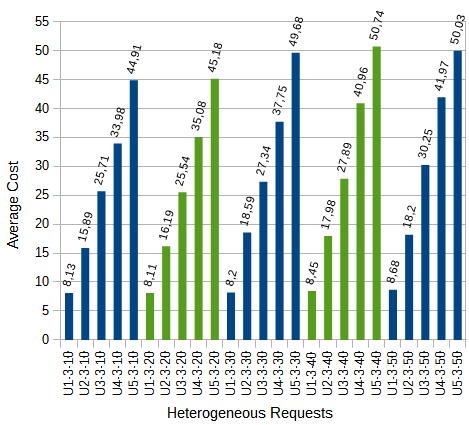
Average costs for requests Un-3-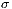 with heterogeneous QoP.
with heterogeneous QoP.
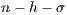 for the Test 3.
for the Test 3.
7 Conclusions and Future Work
In this paper we have proposed a paradigm for quantifying the grade of protection service in a generic way. Protection resources can be dedicated and shared. The first scheme shows 100% recovery and is it warranted by dedicated protection. The second scheme is associated with a measure based on recovery probability, which indicates the grade of conflict among users with shared resources. Basically, in this work the recovery probability concept is proposed to be used in order to define different grade of conflicts which conform a set of QoP levels.
The FLSA algorithm, based on Genetic Algorithm, was developed to solve the RWA-PLF problem with the flexible QoP approach. FLSA calculates primary and backup lightpaths, considering the QoP requirement of each unicast request and the set of pre-defined QoP levels.
These preliminary experimental results have shown that the proposal provides flexibility at the moment to define the QoP levels before the optimization process. Thus, the network administrator can determine the QoP levels necessary for business with the following advantage: flexibility in the definition of the business, by having a list of available and adjustable QoP levels. This will finally allow a fair administration of the assigned resources, from the viewpoint of the customer, i.e. customers pay a service in according to QoP level nearest to requested.
Future work will consider the analysis of other QoS variables to create new and more elaborate QoP metrics. On the other hand, it is necessary to perform experimental environment in a pure multi-objective optimization context [22] to study the impact among object functions in conflicts. It is also important to consider other network topologies, multicast traffic and more rigorous statistical tests [23].
Acknowledgements
We would like to thank Lucia Ibañez, head of the Idiomatik Department (FPUNA), who helped to improve the English structure of this paper.
References
[1] A. Somani, Survivability and Traffic Grooming in WDM Optical Networks. Cambridge University Press, 2005. [Online]. Available: http://books.google.es/books?id=-pxPJdeseVsC
[2] C. Núñez, B. Barán, and D. P. Pinto-Roa, “Asignación óptima de Lightpath bajo requerimientos de QoS. Un enfoque multiobjetivo basado en MOEAs.” in XXXIII Conferencia Latinoamericana en Informática CLEI 2007, 2007.
[3] A. Tanenbaum, Redes de Computadoras. Pearson Education, 2003. [Online]. Available: http://books.google.com.py/books?id=d_m3W_Yob8kC
[4] N. Golmie, T. D. Ndousse, and D. H. Su, “A differentiated optical services model for WDM networks,” Communications Magazine, IEEE, vol. 38, no. 2, pp. 68–73, 2000.
[5] D. Hillerkuss, R. Schmogrow, M. Meyer, S. Wolf, M. Jordan, P. Kleinow, N. Lindenmann, P. C. Schindler, A. Melikyan, X. Yang et al., “Single-laser 32.5 Tbit/s Nyquist WDM transmission,” Optical Communications and Networking, IEEE/OSA Journal of, vol. 4, no. 10, pp. 715–723, 2012.
[6] B. Mukherjee, Optical WDM Networks, ser. Optical Networks. Springer, 2006. [Online]. Available: http://books.google.es/books?id=1NZ2zNEyQTwChttp://books.google.es/books?id=1NZ2zNEyQTwC
[7] J. Huang, X. Huang, and Y. Ma, “Routing with multiple quality-of-services constraints: An approximation perspective,” J. Netw. Comput. Appl., vol. 35, no. 1, pp. 469–479, Jan. 2012. [Online]. Available: http://dx.doi.org/10.1016/j.jnca.2011.09.009
[8] O. Gerstel and G. H. Sasaki, “Quality of protection (QoP): a quantitative unifying paradigm to protection service grades,” in OptiComm 2001: Optical Networking and Communications Conference. International Society for Optics and Photonics, 2001, pp. 12–23.
[9] I. Pujol, “Contribuciones al diseño de redes ópticas de nueva generación: Protección, calidad de servicio y eficiencia energética,” Ph.D. dissertation, Universidad Carlos III de Madrid, Abril 2012.
[10] D. P. Pinto-Roa, B. Barán, and C. A. Brizuela, “Wavelength converter allocation in optical networks: An evolutionary multi-objective optimization approach,” in Intelligent Systems Design and Applications, 2009. ISDA ’09. Ninth International Conference on, Nov 2009, pp. 414–419.
[11] K. Zhu, H. Zhu, and B. Mukherjee, Traffic grooming in optical WDM mesh networks. Springer, 2005.
[12] M. To and P. Neusy, “Unavailability analysis of long-haul networks,” Selected Areas in Communications, IEEE Journal on, vol. 12, no. 1, pp. 100–109, 1994.
[13] R. Saeedinia, “Protection switching in communication networks,” in Networks and Optical Communications (NOC), 2011 16th European Conference on. IEEE, 2011, pp. 20–23.
[14] S. Zhong and A. Jaekel, “Optimal priority-based lightpath allocation for survivable WDM networks,” in Computer Communications and Networks, 2004. ICCCN 2004. Proceedings. 13th International Conference on. IEEE, 2004, pp. 17–22.
[15] A. Talia, G. Villalba, E. Dávalos, and D. P. Pinto-Roa, “Optimal selection of p-cycles on WDM optical networks with shared risk link group independent restorability using genetic algorithm,” Latin America Transactions, IEEE, vol. 10, no. 1, pp. 1385–1390, 2012.
[16] S. Ramamurthy, L. Sahasrabuddhe, and B. Mukherjee, “Survivable WDM mesh networks,” Journal of Lightwave Technology, vol. 21, no. 4, p. 870, 2003.
[17] N. K. Singhal, L. H. Sahasrabuddhe, and B. Mukherjee, “Provisioning of survivable multicast sessions against single link failures in optical WDM mesh networks,” Journal of lightwave technology, vol. 21, no. 11, p. 2587, 2003.
[18] H. Alazemi, S. Sebbah, and M. Nurujjaman, “Fast and efficient network protection method using path pre-cross-connected trails,” Optical Communications and Networking, IEEE/OSA Journal of, vol. 5, no. 12, pp. 1343–1352, Dec 2013.
[19] S. il Kim and S. Lumetta, “Protection Based QoS in WDM Mesh Networks,” Coordinated Science Laboratory, University of Illinois at Urbana-Champaign, Tech. Rep., 2006.
[20] D. E. Goldberg et al., Genetic algorithms in search, optimization, and machine learning. Addison-wesley Reading Menlo Park, 1989, vol. 412.
[21] C. A. C. Coello, D. A. Van Veldhuizen, and G. B. Lamont, Evolutionary algorithms for solving multi-objective problems. Springer, 2002, vol. 242.
[22] X.-S. Yang, S. F. Chien, and T. O. Ting, Bio-inspired Computation in Telecommunications. Morgan Kaufmann, 2015.
[23] D. J. Sheskin, Handbook of parametric and nonparametric statistical procedures. CRC Press, 2003.












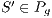

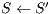
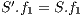 and
and 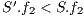
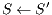
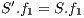 and
and 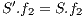 and
and 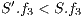
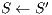
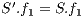 and
and 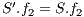 and
and 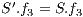 and
and 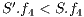
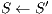
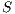 ;
;